Hello, I am Jonathan Vargas
I am a senior undergraduate student at the University of Texas at San Antonio studying Cyber Security and Information Systems. I am enthusiastic about hardening operating systems and network security and strive to lead the next generation of cyber security professionals. My motivation to build strong, secure networks derives from a robust desire to ensure our private data remains private.
Throughout this site, you will find various articles I have authored involving penetration testing methodologies and write ups for vulnerable machines on Hack The Box and Try Hack Me. For further information on my academic and professional achievements, please review my resume with the button below.
CTF | Wargames | OverTheWire | HTB | THM

For the past five years, learning offensive and defensive cyber security skills online has become as attainable as picking up a book from the library. Except these books are not only pages of content; some are full fledged wargame simulations.
Networks | CTF | OpenVPN | Vulnhub

Finding any tutorials on how to configure an OpenVPN server for Vulnhub CTF practice has proven to be more difficult than the search for bigfoot. In order for future enthusiasists like myself to have an easier time getting a VPS running, here is my guide
OSCP | Certs | Red Team | Professional Development

The OSCP is a coveted, well-known title bestowed upon individuals who endure a daunting 24-hour penetration test on a simulated network of five servers. Although I cannot speak on the actual exam process, I am excited to offer advice on how a student in my position 6 months ago can better prepare themselves for this test.
Apache | Web apps | Linux | CGI
This is my second article in the "Field Reference" series. The following's intended use is to be quickly reviewed during pentesting engagements, meaning most simple subjects will not be elaborated on due to unpredictable variables in each machine's environment.
Juicy Potato | Rotten Potato | Windows | Services
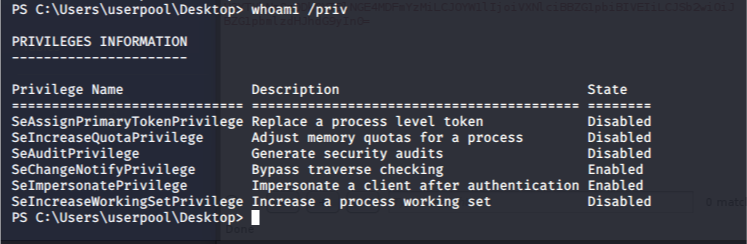
If you have obtained a shell as NT AUTHORITY \ LOCAL SERVICE with SeImpersonateToken enabled, you are SYSTEM. Leverage the OSCP-friendly Juicy Potato exploit to throw back a system shell to your netcat listener. This guide serves as a quick field reference when testing vulnerable windows machines.
CTF | Writeup | Try Hack Me | sudoedit | symbolic link

Explore the repurcussions of having a password hint, automating the creation of a custom password list using Python, brute forcing a login page with OWASP ZAP, pivoting between three different users on the system, and exploiting a sudoedit wildcard path vulnerability using a symbolic link attack.
CTF | Methodologies | Redis | Databases | Try Hack Me

Res is a Try Hack Me room serving as a surface level introduction to pentesting the Redis database management system. Redis is a free, open-sourced, DBMS that provides data storage for processes, applications, and servers with an in-memory data structure. In this writeup, we will be exploring how to pentest a remote Redis instance with unauthenticated login enabled: the cause of server exploitation.
CVE | CTF | OpenBSD | Port 80 | SSH Keys | Cookies

Insecure cookies and out-of-date operating systems make for a scary combination when it comes to preventing your site from data breaches and takeovers. In this POC report, we will prove a vulnerability that exists in the OpenBSD kernel version 6.6 for httpd services.
OSINT | Maps | Packet Analysis | Privacy

For every Google account created, several identification numbers and aliases are tied to that account and will be used as a pointer for most ensuing Google HTTP posts and requests.
RCE | Windows XP | SMB | Nmap | Dir Busting | CVE
This proof of concept (POC) report demonstrates why maintaining a data-sharing server on an outdated operating system is the technological equivalent of hiding your house keys under the doormat. Here is why it is vital for IT managers to implement automated patch update policies to hosting data on compromised systems.









